If your iPhone isn’t running iOS 17.4 or later, you need to update it now to keep the cops out

While Apple never included it in the release notes for iOS 17.4, this version of the iPhone’s operating system included a way to block Cellebrite machines used by law enforcement to unlock iPhone handsets. The FBI and even local police have employed the Cellebrite device to gather evidence that was locked inside an iPhone. Apple and Cellebrite go back and forth with Apple blocking the Israeli-made machine and Cellebrite finding a way in.
A new report says that based on leaked Cellebrite documentation, the company’s machines are unable to unlock iPhone units running iOS 17.4 or later using its brute force technique. Cellebrite is doing research to see how it can break into iOS builds released since early March. The iOS 17.4 update is known for making changes to the iPhone in the 27 member EU countries allowing Apple to comply with the EU’s Digital Markets Act (DMA). Apple probably will tighten the security screws even more in September when iOS 18 is released.
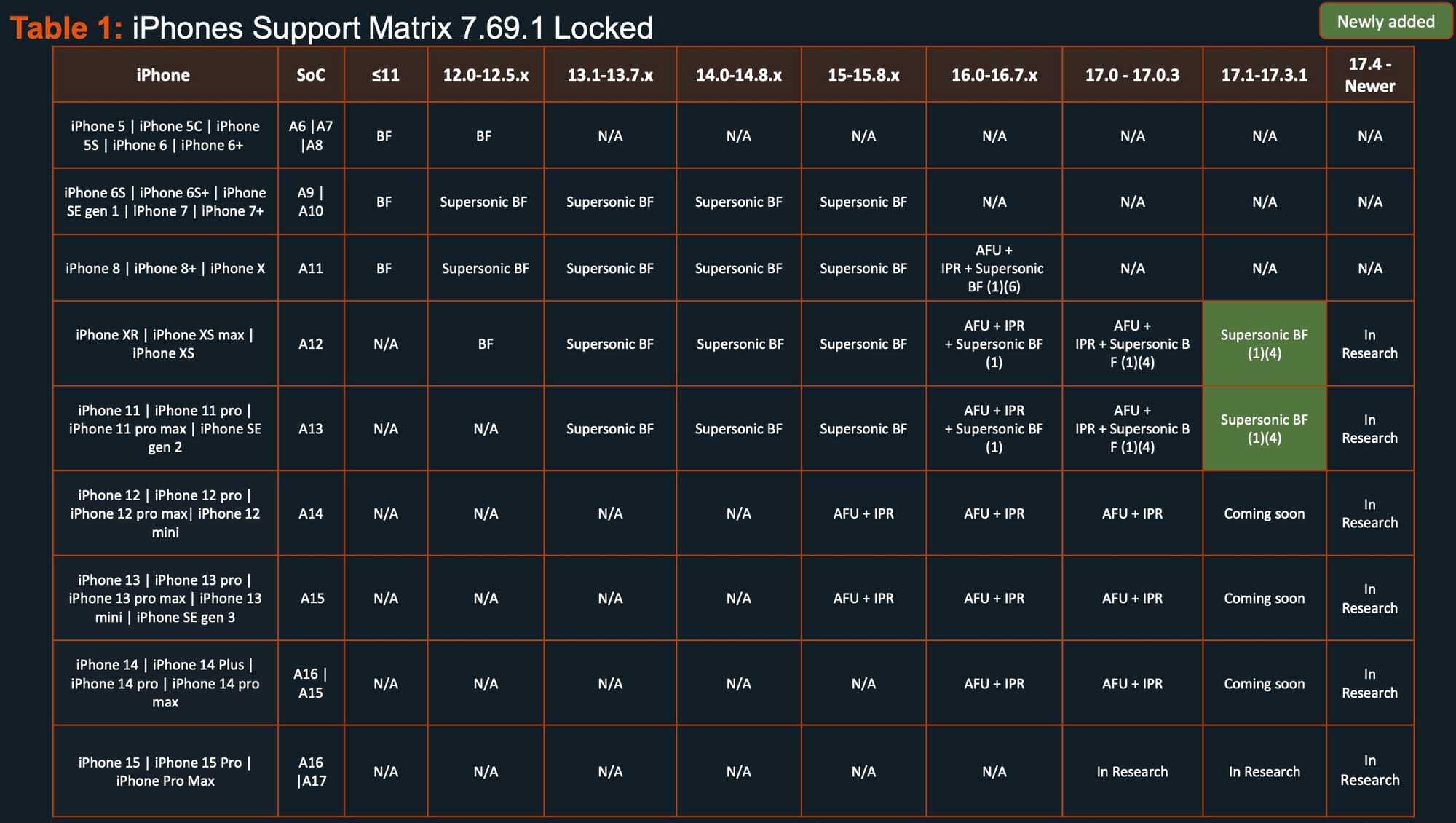
Leaked Cellebrite document shows that the company is working to open iPhones running iOS 17.4 or later. | Image credit-404 Media
The documentation also reveals that Cellebrite will soon be able to unlock iPhone 12 through iPhone 15 iPhone models running iOS 17.1 through iOS 17.3. If you haven’t updated your iPhone lately, perhaps you should do so right away.
The Cellebrite machines override the technology used by Apple to limit the number of passcode attempts that can be tried before the data on an iPhone is erased. Even after this is done, using a brute force attack to figure out the passcode on an iPhone is a slow process. Using a six-digit passcode, there are 1,000,000 possible combinations and Cellebrite’s brute force attack can enter a little over 100 passcodes a day. Cellebrite’s Supersonic Brute Force service can run 40 times faster.
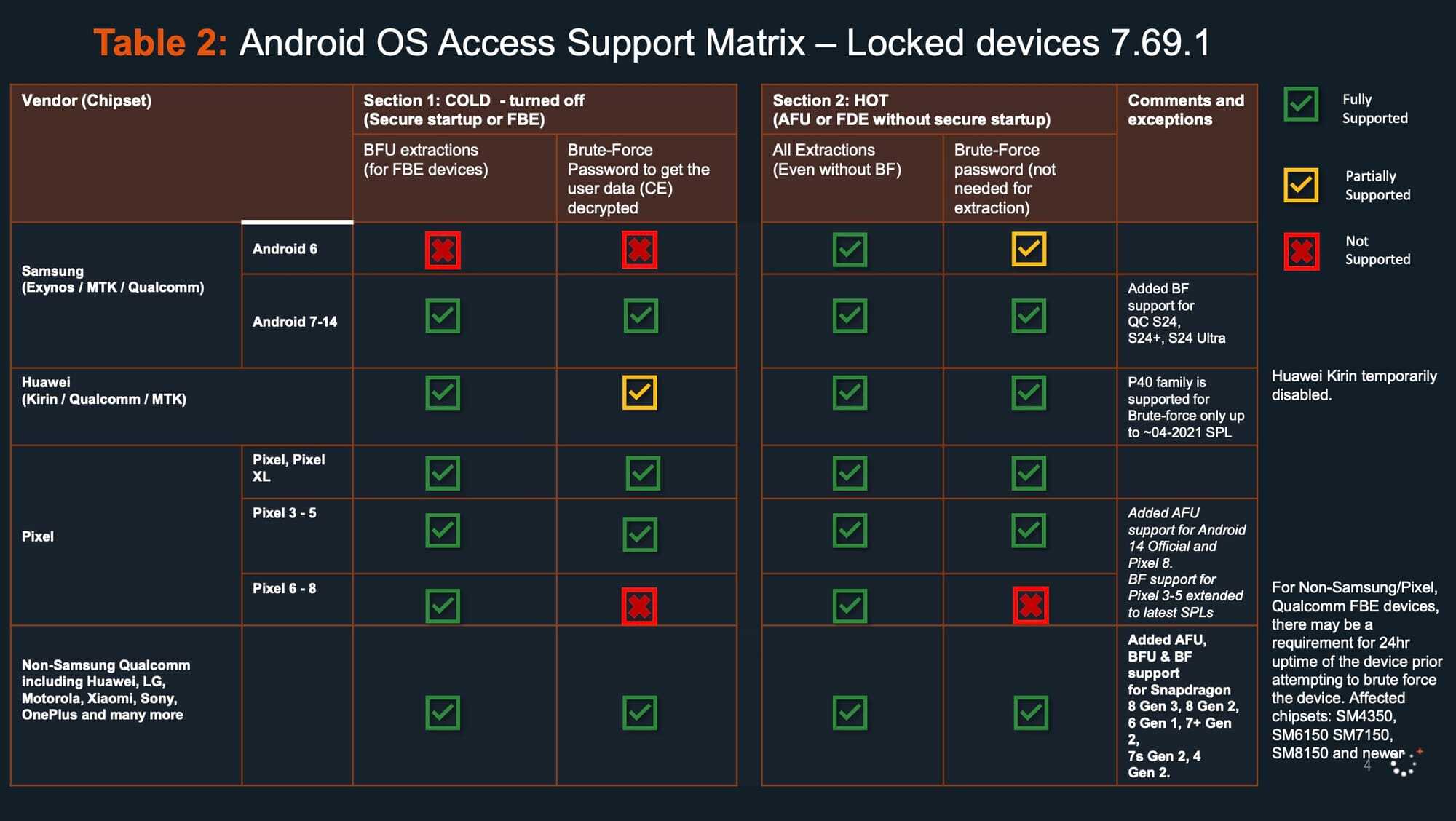
Leaked Cellebrite document reveals which Android devices are vulnerable to Cellebrite’s brute force attack.
Before the machines resort to brute force, they use the phone owner’s birthday, the birthdate of the device owner’s significant other, and other important dates in the owner’s life to try and open the phone. You might not want to base your passcodes on an important date in your life.
As for Android devices, Pixel 6 through Pixel 8 series models cannot be opened by Cellebrite’s brute force if the device being targeted has been turned off. All Samsung models on or turned off using Exynos, MediaTek, or Qualcomm chips running Android 7-14 can be unlocked by brute force. And all non-Samsung Android phones running Android 7-14 are also vulnerable to Cellebrite’s brute force attack.